Computer Architecture Study
This is my revision notes for Computer Architecture. In this post, I will go through some basic knowledge of computer architecture (definitions, theories, calculations), arithmetic operations for computers, pipelined processor design and memory hierarchy. This post will provide a low-level view of computer architecture and design, and help understand how a computer actually runs.
Lecture content
-
Different types of computers
- Personal computers
- Used by an individual
- Server computers
- Used for running larger programs for multiple users, typically accessed only via a network
- Supercomputers
- Used for high-end scientific and engineering calculations
- Embedded computers
- Used for running one pre-determined application or collection of software
- It has stringent limitations on cost or power
- Dependability is achieved primarily through simplicity
- Personal computers
-
Post-PC Era
- Personal mobile device (PMD)
- Cloud computing
-
Levels of program code
- High-level language
- Assembly language
- Hardware representation
-
CPU components
- Data path: performs operations on data
- Control: sequences data path, memory
- Cache memory
- Small fast SRAM memory for immediate access to data
-
Data storage
- Based on memory hierarchy
- Main/primary memory: Memory used to hold programs while they are running
- Secondary memory: Memory used to store programs and data between runs
- Based on if it is volatile or not
- Volatile main memory: lose instructions and data when power off
- SRAM: memory built as an integrated circuit, but faster and less dense than DRAM
- DRAM: memory built as an integrated circuit. It provides random access to any location
- Non-volatile secondary memory: A form of memory that retains data even in the absence of a power source
- Flash memory: a memory that is the standard secondary memory for PMDs. It is slower and much cheaper than DRAM. However, costing more per bit than disks.
- Magnetic disk: also called hard disk which composed of rotating platters coated with a magnetic recording material
- Volatile main memory: lose instructions and data when power off
- Based on memory hierarchy
-
Networks
- Local area network (LAN): Ethernet
- Wide area network (WAN): the internet
- Wireless network: WiFi, Bluetooth
-
Instruction set architecture (architecture)
- An abstract interface between the hardware and the lowest-level software that encompasses all the information necessary to write a machine language program that will run correctly, including instructions, registers, memory access, I/O, and so on.
-
Application binary interface (ABI)
- The user portion of the instruction set plus the operating system interfaces used by application programmers. It defines a standard for binary portability across computers.
-
CPU Clocking
- Clock Period: duration of a clock cycle
- Clock Frequency (rate): cycles per second
-
CPU Time: the time spent processing a given job
- CPU Time = CPU Clock Cycles * Clock Period = CPU Clock Cycles / Clock Frequency
- Performance improved by
- Reducing number of clock cycles
- Increasing clock rate (clock frequency)
-
Clock Cycles = Instruction Count * Clock per Instruction
-
Power = Capacitive load * Voltage2 * Frequency
Background knowledge study
- Byte addressing:
- Each byte of storage has a unique address
- Preferred method for a program to transfer data between a disk controller and memory:
- The program could provide to the disk controller the memory address where the data should be copied. When data is ready to be transferred, the disk controller could use direct memory access to copy the data to memory.
- Speed for data to be transferred over a cable for a computer display:
- 3Gbit/sec
- Steps performed by a CPU to execute instructions:
- Fetch the next instruction from memory: The CPU fetches the next instruction from memory. The instruction is usually stored in a program counter, which contains the memory address of the next instruction to be executed.
- Decode the instruction: The CPU decodes the instruction to determine what operation it needs to perform. This involves identifying the opcode (operation code) of the instruction and any operands (data or memory addresses) that are needed.
- Execute the operations required for the instruction: The CPU performs the operation specified by the instruction. This may involve reading or writing data to memory, performing arithmetic or logical operations on data, or transferring data between different parts of the CPU.
- Repeat for the next instruction: The CPU returns to the fetch step and fetches the next instruction, continuing the cycle.
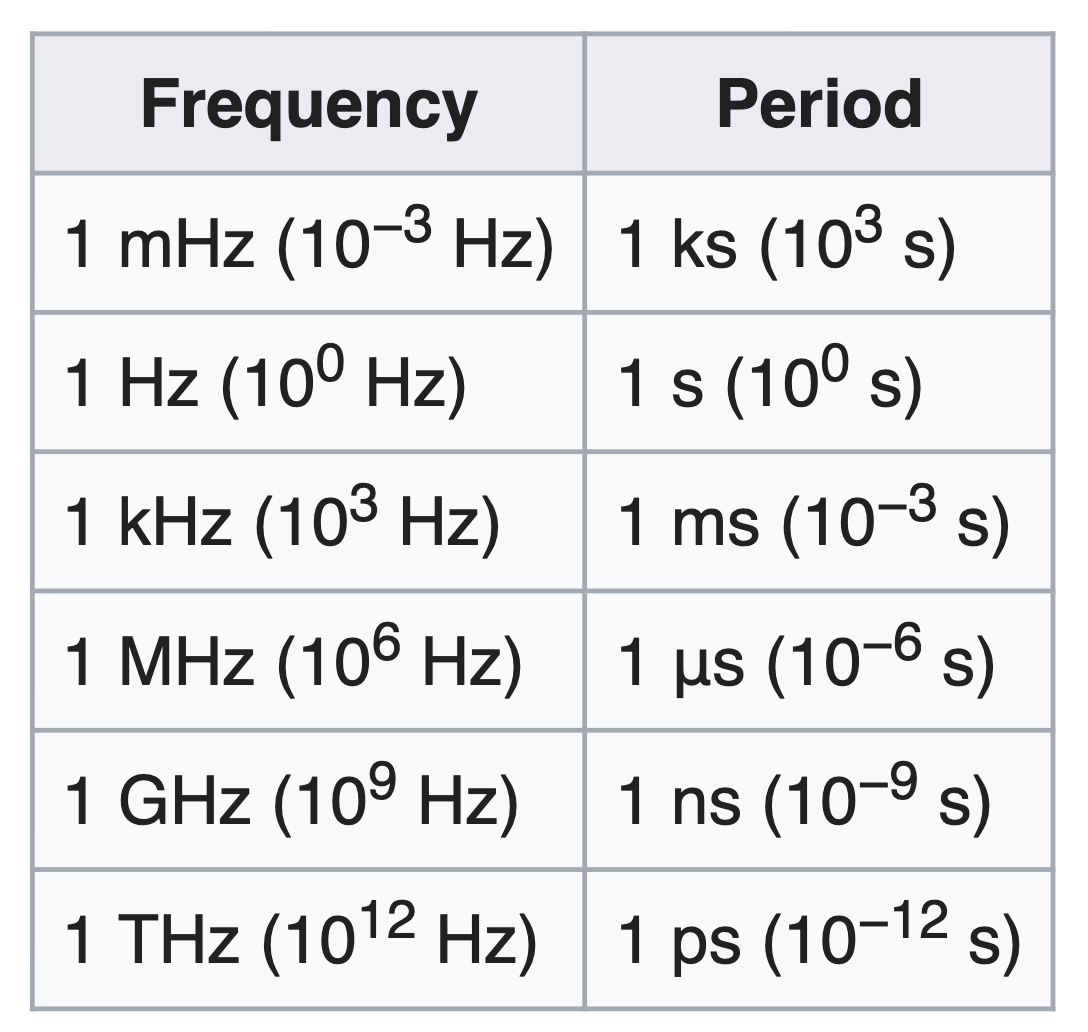
- Period versus frequency:
- How are instructios represented in memory:
- Each instruction is encoded in binary, with specific bit fields encoding the opcode and operands
- Reading a memory involves:
- The CPU determining the memory address
- The CPU transmitting the address to the memory
- The memory retrieving the data at the addressed location
- The memory transmitting the data to the CPU
- SI (International System of Units) multiplier prefixes:

Classes of Exceptions
- Asynchronous exceptions occur as a result of events in I/O devices that are external to the processor. Synchronous exceptions occur as a direct result of executing an instruction.
| Exception Class | Attributes | Cause | Return Behaviour |
|---|---|---|---|
| Interrupt (Async) | Interrupts occur asynchronously as a result of signals from I/O devices that are external to the processor | Signal from I/O device | Always returns to next instruction |
| Trap | Traps are intentional exceptions that occur as a result of executing an instruction. The most use of traps is to provide a procedure-like interface between user programs and the kernel known as a system call. | Internal exception | Always returns to the next instruction |
| Fault | Faults result from error conditions that a handler might be able to correct. If the handler is able to correct the error condition, it returns control to the faulting instruction, thereby re-executing it. Otherwise, the handler returns to an abort routine that terminates the application program that caused the fault | Potentially recoverable error | Might return to current instruction |
| Abort | Aborts result from unrecoverable fatal errors, typically hardware errors such as parity errors that occur when DRAM or SRAM bits are corrupted | Nonrecoverable error | Never returns |